Monday, May 31, 2010
Introducing WebM
-Ganesh Gadde
Introducing WebM, an open web media project:
A key factor in the web’s success is that its core technologies such as HTML, HTTP, TCP/IP, etc. are open and freely implementable. Though video is also now core to the web experience, there is unfortunately no open and free video format that is on par with the leading commercial choices. To that end, we are excited to introduce WebM, a broadly-backed community effort to develop a world-class media format for the open web.
The WebM Project is a Google-sponsored project dedicated to create an open and royalty free video format that provides high quality video compression for use with HTML5 video.The project open source releases WebM related software under a BSD-style license with patent clause. The WebM format consists of the VP8 video codec developed by On2 and the Vorbis audio codec, in a container format based on a profile of Matroska
WebM includes:
- VP8, a high-quality video codec we are releasing today under a BSD-style, royalty-free license
- Vorbis, an already open source and broadly implemented audio codec
- A container format based on a subset of the Matroska media container.
The team that created VP8 have been pioneers in video codec development for over a decade. VP8 delivers high quality video while efficiently adapting to the varying processing and bandwidth conditions found on today’s broad range of web-connected devices. VP8's efficient bandwidth usage will mean lower serving costs for content publishers and high quality video for end-users. The codec's relative simplicity makes it easy to integrate into existing environments and requires less manual tuning to produce high quality results. These existing attributes and the rapid innovation we expect through the open-development process make VP8 well suited for the unique requirements of video on the web.
There are free and commercial tools available for creating and publishing content in the WebM format.- Free and Open Source Tools
- FFmpeg Patches
- DirectShow Filters
- VP8 SDK
- Encoding Parameters
- Encoding Parameters
- GStreamer Plug-ins
- FFmpeg Patches
Playing WebM video:
WebM video files play directly in your web browser using a new technology called HTML5. No plug-ins are required, but you must install a web browser that supports WebM files.
What’s great about WebM
- Very high quality video
- Great video playback performance, even on older computers
- 100% free and open to everyone
- Supported on popular video sites like YouTube
How to Play WebM Video
Playing on YouTube
- Download and install a supported browser (listed below).
- Start the newly installed browser.
- Go to www.youtube.com/html5 and enroll in the YouTube HTML5 experiment.
- Search for a video by keyword. For example, trailers.
- In the browser’s address bar, add
&webm=1to the end of the URL. For example,http://www.youtube.com/results?search_query=trailers&aq=f&webm=1. - Press Enter.
- In the list of videos that appears, click any of the links.
- The video will play in your browser and display HTML5 webm in the toolbar of the video player.
Supported Web Browsers
- Mozilla Firefox nightly WebM build
- Opera Labs
- Google Chrome Early Access Release Channel
- Chromium tip/nightly trunk build
Other Media Players
- VLC
- Moovida Core
Sunday, May 30, 2010
HTML5
--Srikanth Pulicherla
Introduction:
HTML5 is the fifth major revision of the core language of the World Wide Web, HTML. HTML4 became a W3C Recommendation in 1997. HTML grew hardly at all in next eight years. In 2004 Apple, Mozilla and Opera formed Web Hypertext Application Technology Working Group (WHATWG) and started working on new version of HTML. Then in 2006 W3C took note of these developments and indicated an interest to participate in the development of HTML5. WHATWG allowed the W3C to publish the specification under the W3C copyright. Since then, both groups have been working together. Main goals of WHATWG include media independence (reducing plug-in dependency), clear documentation of browser behavior, developing new practical features to reduce the complexity and of course backward compatibility.
Enhancements:
1.Structure and semantics
2. Embedded Content and Multimedia
3. DOM APIs
4. Forms
5. Repetition model.
1. Structure and Semantics
a) Structure
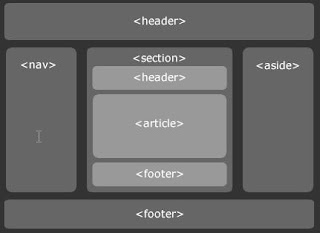
Even well-formed HTML pages are harder to process than they should be because of the lack of structure. You have to figure out where the section breaks go by analyzing header levels. Sidebars, footers, headers, navigation menus, main content sections, and all the individual stories are marked up by the div element. HTML 5 adds new elements to specifically identify each of these common constructs.
• section
• header
• footer
• nav
• article
b) Semantics
HTML 4 has five different inline elements to represent subtly different variations of computer code: var, code, kbd, tt, and samp. However, it doesn't have any way to indicate such basic qualities as time, numbers. HTML 5 aims to rectify this imbalance between techies and normal writers with several new inline elements.
mark
The m element indicates text that is "marked" somehow but not necessarily emphasized. You can imagine it as being like highlighted passages in a book. The canonical use case is Google's cached pages. When you follow a link to the cached copy, the search terms are marked. For example, if you searched for "Egret", then a cached Google page might be marked up like this
The Great <mark>Egret</mark> (also known as theAmerican <mark>Egret</mark>)
is a large white wading bird found worldwide.
The Great <mark>Egret</mark> flies with slow wing beats.
The scientific name of the Great <mark>Egret</mark> is <i>Casmerodiusalbus</i>
Time
The time element indicates a specific moment in history, such as 5:35 P.M., EST, April 23, 2007. For example
<p>I am writing this example at
<time>5:35 P.M. on April 23rd</time>.
</p>
The time element helps browsers and others recognize times in HTML pages. It doesn't require any particular format for the element's content. However, each time element should have a datetime attribute that includes the time in a more machine-recognizable form, like this
<p>I am writing this example at
<time datetime="2007-04-23T17:35:00-05:00">5:35 P.M. on April 23rd</time>.
</p>
Machine-readable times are potentially useful for search engines, calendar programs, and the like.
Meter
The meter element represents a numeric value in a specified range. For example, you can use it for salaries, percentage of the French electorate that voted for Le Pen, or test scores. Here, I use meter to mark up some data I got from a Google programmer at Software Development 2007:
<p>An entry level programmer in Silicon Valley
Can expect to start around <meter>$90,000</meter> per year.
</p>
The meter element helps browsers and other clients recognize amounts in HTML pages. It doesn't require any particular format for the element's content. However, each meter element can have up to six attributes offering information about this amount in a more machine-recognizable form.
<p>Your score was
<meter value="88.7" min="0" max="100" low="65" high="96" optimum="100">B+</meter>.
</p>
Progress
The progress element represents the state of an ongoing process, like the progress bar in a graphical user interface (GUI) application. For instance, it can show you what percentage of a file is downloaded or how far you are into a movie. This progress control says that a download is 33% complete:
<p>Downloaded:
<progress value="1534602" max="4603807">33%</progress>
</p>
The value attribute shows the current state of the operation. The max attribute shows the total amount toward which the progress is moving. Here the element indicates that 1,534,602 bytes out of a total 4,603,807 bytes have been downloaded.
You can display indefinite progress bars by omitting the max attribute.
You should use the JavaScript language to dynamically update the progress bar as the operation continues. Statically, this element isn't very interesting.
Sample progress bar may look like
2. Embedded Content and Multimedia
HTML5 video and audio:
One of the main goals of HTML5 is to reduce the need for proprietary plug-in-based rich internet application (RIA) technologies such as Adobe Flash and Microsoft Silverlight. Currently there is no standard format to embed video on web. HTML5 video is intended to become the new standard way to show video online, but to do so it’s required to specify at least one video format that all the browsers should support in video format.
Default video format debate:
The Default video format should be selected based on
“It would be helpful for interoperability if all browsers could support the same codecs. However, there are no known codecs that satisfy all the current players: we need a codec that is known to not require per-unit or per-distributor licensing, that is compatible with the open source development model, that is of sufficient quality as to be usable, and that is not an additional submarine patent risk for large companies. This is an ongoing issue and this section will be updated once more information is available.”
Although Theora is not affected by known patents, companies such as Apple and (reportedly) Nokia are concerned about unknown patents that might affect it, whose owners might be waiting for a corporation with deep pockets to use the format before suing. Formats like H.264 might also be subject to unknown patents in principle, but they have been deployed much more widely and so it is presumed that any patent-holders would have already sued someone. Apple has also opposed requiring Ogg format support in the HTML standard on the grounds that some devices might support other formats much more easily, and that HTML has historically not required particular formats for anything.
Some web developers criticized the removal of the Ogg formats from the specification. A follow-up discussion also occurred on the W3C questions and answers blog.
H.264/MPEG-4 AVC is widely used, and has good speed, compression, hardware decoders, and video quality, but is covered by patents. Except in some particular cases, users of H.264 have to pay licensing fees to the MPEG LA, a group of patent-holders including Microsoft and Apple. As a result, it has not been considered as a required default codec.
Google acquisition of ON2 resulted in WebM project a royalty-free, open source release of VP8. This format is supported by Google Chrome, Opera and Mozilla Firefox.
Example:
<audio src="horse.ogg" controls="controls">
Your browser does not support the audio element.
</audio>
<video src="movie.ogg" width="320" height="240" controls="controls">
Your browser does not support the video tag.
</video>
Content between the <video> and </video> tags shown in browsers without HTML5.
canvas
Example:
<canvas id="myCanvas" width="200" height="100"></canvas>
<script type="text/javascript">
var c=document.getElementById("myCanvas");
var cxt=c.getContext("2d");
cxt.fillStyle="#FF0000";
cxt.fillRect(0,0,150,75);
Advantages:
3. DOM APIs
2. Stock ticker updates
4. Forms
Form Controls
HTML 4 controls are too limited.Several new types added in HTML5.
Dates and Times
<input type="datetime">
<input type="date">
<input type="time">
Numbers and range
<input type="number">
<input type="range">
Email and URIs
<input type="email">
<input type="url">
Combo Boxes
<input list="title-list">
<datalist id="title-list">
<option value="...">
</datalist>
Form Validations
1. New attributes are added to describe validity constraints for the expected input.
Example: required, pattern, min, max, etc.
2. New DOM APIs allow scripts to detect and deal with user input errors more easily.
5. Repetition Model
Occasionally, a form may need a section to be repeated an arbitrary number of times. For example, an order form could have one row per item. Traditionally, this has been implemented either by using complex client-side scripts or by sending a request to the server for every new row. Using the HTML5 repetition model problem is reduced to describing a template in the mark-up, and then specifying where and when that template should be repeated.
Future
HTML 5 is part of the future of the Web. Its new elements enable clearer, simpler markup that makes pages more obvious. Although not all browsers will support these new elements at first, the same has been true for most elements introduced after HTML was first invented: img, table, object, and many more. Support will come with time. At least by 2011 we will see all the browsers supporting HTML5. In the meantime, HTML's backward compatibility ensures users with legacy browsers will still be able to read HTML 5 pages. They can do so today. Users with more modern browsers will get an enhanced experience, but no one will be left out.
Introduction:
HTML5 is the fifth major revision of the core language of the World Wide Web, HTML. HTML4 became a W3C Recommendation in 1997. HTML grew hardly at all in next eight years. In 2004 Apple, Mozilla and Opera formed Web Hypertext Application Technology Working Group (WHATWG) and started working on new version of HTML. Then in 2006 W3C took note of these developments and indicated an interest to participate in the development of HTML5. WHATWG allowed the W3C to publish the specification under the W3C copyright. Since then, both groups have been working together. Main goals of WHATWG include media independence (reducing plug-in dependency), clear documentation of browser behavior, developing new practical features to reduce the complexity and of course backward compatibility.
Enhancements:
1.Structure and semantics
2. Embedded Content and Multimedia
3. DOM APIs
4. Forms
5. Repetition model.
1. Structure and Semantics
a) Structure
Even well-formed HTML pages are harder to process than they should be because of the lack of structure. You have to figure out where the section breaks go by analyzing header levels. Sidebars, footers, headers, navigation menus, main content sections, and all the individual stories are marked up by the div element. HTML 5 adds new elements to specifically identify each of these common constructs.
• section
• header
• footer
• nav
• article

b) Semantics
HTML 4 has five different inline elements to represent subtly different variations of computer code: var, code, kbd, tt, and samp. However, it doesn't have any way to indicate such basic qualities as time, numbers. HTML 5 aims to rectify this imbalance between techies and normal writers with several new inline elements.
mark
The m element indicates text that is "marked" somehow but not necessarily emphasized. You can imagine it as being like highlighted passages in a book. The canonical use case is Google's cached pages. When you follow a link to the cached copy, the search terms are marked. For example, if you searched for "Egret", then a cached Google page might be marked up like this
The Great <mark>Egret</mark> (also known as theAmerican <mark>Egret</mark>)
is a large white wading bird found worldwide.
The Great <mark>Egret</mark> flies with slow wing beats.
The scientific name of the Great <mark>Egret</mark> is <i>Casmerodiusalbus</i>
Time
The time element indicates a specific moment in history, such as 5:35 P.M., EST, April 23, 2007. For example
<p>I am writing this example at
<time>5:35 P.M. on April 23rd</time>.
</p>
The time element helps browsers and others recognize times in HTML pages. It doesn't require any particular format for the element's content. However, each time element should have a datetime attribute that includes the time in a more machine-recognizable form, like this
<p>I am writing this example at
<time datetime="2007-04-23T17:35:00-05:00">5:35 P.M. on April 23rd</time>.
</p>
Machine-readable times are potentially useful for search engines, calendar programs, and the like.
Meter
The meter element represents a numeric value in a specified range. For example, you can use it for salaries, percentage of the French electorate that voted for Le Pen, or test scores. Here, I use meter to mark up some data I got from a Google programmer at Software Development 2007:
<p>An entry level programmer in Silicon Valley
Can expect to start around <meter>$90,000</meter> per year.
</p>
The meter element helps browsers and other clients recognize amounts in HTML pages. It doesn't require any particular format for the element's content. However, each meter element can have up to six attributes offering information about this amount in a more machine-recognizable form.
- value
- min
- low
- high
- max
- optimum
<p>Your score was
<meter value="88.7" min="0" max="100" low="65" high="96" optimum="100">B+</meter>.
</p>
This indicates that the student's score was 88.7 out of a possible 100. The lowest possible grade was 0, but the lowest actual grade anyone got was 65. The highest grade anyone got was 96, although of course the ideal score was 100. User agents can display this information using some sort of meter control or give the extra data in a tooltip, but most will probably style it like any other inline element.
HTML5 meter may look like
HTML5 meter may look like
Progress
The progress element represents the state of an ongoing process, like the progress bar in a graphical user interface (GUI) application. For instance, it can show you what percentage of a file is downloaded or how far you are into a movie. This progress control says that a download is 33% complete:
<p>Downloaded:
<progress value="1534602" max="4603807">33%</progress>
</p>
The value attribute shows the current state of the operation. The max attribute shows the total amount toward which the progress is moving. Here the element indicates that 1,534,602 bytes out of a total 4,603,807 bytes have been downloaded.
You can display indefinite progress bars by omitting the max attribute.
You should use the JavaScript language to dynamically update the progress bar as the operation continues. Statically, this element isn't very interesting.
Sample progress bar may look like
2. Embedded Content and Multimedia
HTML5 video and audio:
One of the main goals of HTML5 is to reduce the need for proprietary plug-in-based rich internet application (RIA) technologies such as Adobe Flash and Microsoft Silverlight. Currently there is no standard format to embed video on web. HTML5 video is intended to become the new standard way to show video online, but to do so it’s required to specify at least one video format that all the browsers should support in video format.
Default video format debate:
The Default video format should be selected based on
- Good compression and video clarity.
- Decode processor usage.
- Should be royalty-free
“It would be helpful for interoperability if all browsers could support the same codecs. However, there are no known codecs that satisfy all the current players: we need a codec that is known to not require per-unit or per-distributor licensing, that is compatible with the open source development model, that is of sufficient quality as to be usable, and that is not an additional submarine patent risk for large companies. This is an ongoing issue and this section will be updated once more information is available.”
Although Theora is not affected by known patents, companies such as Apple and (reportedly) Nokia are concerned about unknown patents that might affect it, whose owners might be waiting for a corporation with deep pockets to use the format before suing. Formats like H.264 might also be subject to unknown patents in principle, but they have been deployed much more widely and so it is presumed that any patent-holders would have already sued someone. Apple has also opposed requiring Ogg format support in the HTML standard on the grounds that some devices might support other formats much more easily, and that HTML has historically not required particular formats for anything.
Some web developers criticized the removal of the Ogg formats from the specification. A follow-up discussion also occurred on the W3C questions and answers blog.
H.264/MPEG-4 AVC is widely used, and has good speed, compression, hardware decoders, and video quality, but is covered by patents. Except in some particular cases, users of H.264 have to pay licensing fees to the MPEG LA, a group of patent-holders including Microsoft and Apple. As a result, it has not been considered as a required default codec.
Google acquisition of ON2 resulted in WebM project a royalty-free, open source release of VP8. This format is supported by Google Chrome, Opera and Mozilla Firefox.
Example:
<audio src="horse.ogg" controls="controls">
Your browser does not support the audio element.
</audio>
<video src="movie.ogg" width="320" height="240" controls="controls">
Your browser does not support the video tag.
</video>
Content between the <video> and </video> tags shown in browsers without HTML5.
canvas
The canvas element is used to draw graphics on a web page. It uses javascript to draw graphics on web page.
Example:
<canvas id="myCanvas" width="200" height="100"></canvas>
<script type="text/javascript">
var c=document.getElementById("myCanvas");
var cxt=c.getContext("2d");
cxt.fillStyle="#FF0000";
cxt.fillRect(0,0,150,75);
</script>
Advantages:
- Dynamic and interactive graphics.
- Draw images using 2D drawing API.
- Lines, curves, shapes, fills(as in MS paint)
- Useful for Graphs, applications, games and puzzles etc.
Graphs using HTML5 canvas may look like
3. DOM APIs
- Allows immediate update notification from server to client
- Send any arbitrary data to the client, intended to be processed by a script
- Update content without reloading page
- Useful for
2. Stock ticker updates
4. Forms
Form Controls
HTML 4 controls are too limited.Several new types added in HTML5.
Dates and Times
<input type="datetime">
<input type="date">
<input type="time">
Numbers and range
<input type="number">
<input type="range">
Email and URIs
<input type="email">
<input type="url">
Combo Boxes
<input list="title-list">
<datalist id="title-list">
<option value="...">
</datalist>
Form Validations
1. New attributes are added to describe validity constraints for the expected input.
Example: required, pattern, min, max, etc.
2. New DOM APIs allow scripts to detect and deal with user input errors more easily.
5. Repetition Model
Occasionally, a form may need a section to be repeated an arbitrary number of times. For example, an order form could have one row per item. Traditionally, this has been implemented either by using complex client-side scripts or by sending a request to the server for every new row. Using the HTML5 repetition model problem is reduced to describing a template in the mark-up, and then specifying where and when that template should be repeated.
Future
HTML 5 is part of the future of the Web. Its new elements enable clearer, simpler markup that makes pages more obvious. Although not all browsers will support these new elements at first, the same has been true for most elements introduced after HTML was first invented: img, table, object, and many more. Support will come with time. At least by 2011 we will see all the browsers supporting HTML5. In the meantime, HTML's backward compatibility ensures users with legacy browsers will still be able to read HTML 5 pages. They can do so today. Users with more modern browsers will get an enhanced experience, but no one will be left out.
Friday, May 28, 2010
UML Concepts(Continuation...)
-Satya Swati
6) Activity Diagram:
The easiest way to visualize an Activity diagram is to think of a flowchart of a code. The flowchart is used to depict the business logic flow and the events that cause decisions and actions in the code to take place.
Activity diagrams represent the business and operational work flows of a system. An Activity diagram is a dynamic diagram that shows the activity and the event that causes the object to be in the particular state.
So, what is the importance of an Activity diagram, as opposed to a State diagram? A State diagram shows the different states an object is in during the life cycle of its existence in the system, and the transitions in the states of the objects. These transitions depict the activities causing these transitions, shown by arrows.
An Activity diagram talks more about these transitions and activities causing the changes in the object states.
Elements of an Activity diagram
Significance:
- Addresses a dynamic view of the system.
- Important for modeling system functions.
- Emphasizes the flow of objects and synchronization of the flow in support of parallel processing.
- An extension of the old "flow chart" diagram combined with Petri nets.
7) Package diagram:
A package diagram in the UMLdepicts the dependencies between the packages that make up a model.In addition to the standard UML Dependency relationship, there are two special types of dependencies defined between packages:
package import
package merge
A package import is "a relationship between an importing namespace and a package, indicating that the importing namespace adds the names of the members of the package to its own namespace." [1] By default, an unlabeled dependency between two packages is interpreted as a package import relationship.
A package merge is "a directed relationship between two packages, that indicates that the contents of the two packages are to be combined. It is very similar to Generalization in the sense that the source element conceptually adds the characteristics of the target element to its own characteristics resulting in an element that combines the characteristics of both"
Package diagrams can use packages containing use cases to illustrate the functionality of a software system.
Package diagrams can use packages that represent the different layers of a software system to illustrate the layered architecture of a software system. The dependencies between these packages can be adorned with labels / stereotypes to indicate the communication mechanism between the layers.
Significance:
- Addresses larger system engineering issues, and package dependence.
8) Component Diagram:
The different high-level reusable parts of a system are represented in a Component diagram. A component is one such constituent part of a system. In addition to representing the high-level parts, the Component diagram also captures the inter-relationships between these parts.
So, how are component diagrams different from the previous UML diagrams that we have seen? The primary difference is that Component diagrams represent the implementation perspective of a system. Hence, components in a Component diagram reflect grouping of the different design elements of a system, for example, classes of the system.
Let us briefly understand what criteria to apply to model a component. First and foremost, a component should be substitutable as is. Secondly, a component must provide an interface to enable other components to interact and use the services provided by the component. So, why would not a design element like an interface suffice? An interface provides only the service but not the implementation. Implementation is normally provided by a class that implements the interface. In complex systems, the physical implementation of a defined service is provided by a group of classes rather than a single class. A component is an easy way to represent the grouping together of such implementation classes.
You can model different types of components based on their use and applicability in a system. Components that you can model in a system can be simple executable components or library components that represent system and application libraries used in a system. You also can have file components that represent the source code files of an application or document files that represent, for example, the user interface files such as HTML or JSP files. Finally, you can use components to represent even the database tables of a system as well!
Now that we understand the concepts of a component in a Component diagram, let us see what notations to use to draw a Component diagram.
Elements of a Component Diagram:
Significance:
- Shows organization and dependencies among a set of components.
- Components are composed of one or more classes or interfaces.
- A static view of the system implementation.
The Deployment Diagram:
After all the UML diagrams that we have seen till now, you might groan—one more UML diagram? Well, until now we have discussed UML diagrams that cover the application side in terms of both static and dynamic behavior. The component diagram that we covered in the previous article still focused on the representation of the physical implementation of the application components that perform and provide required functionality. The deployment diagram provides a different perspective of the application. The deployment diagram captures the configuration of the runtime elements of the application.
This diagram is by far more useful when a system is built and ready to be deployed. But, this does not mean that you should start on your deployment diagram after your system is built. On the contrary, your deployment diagram should start from the time your static design is being formalized using, say, class diagrams. This deployment diagram then evolves and is revised until the system is built. It is always a best practice to have visibility of what your deployment environment is going to be before the system is built so that any deployment-related issues are identified to be resolved and not crop up at the last minute. The general rule of thumb is that correction costs due to changes increase as the project nears completion.
So, how are deployment diagrams and component diagrams related? Essentially, the components in a component diagram are contained in the deployment diagram elements. Hence, while components provide the application functionality, the deployment diagram elements provide the necessary environment for the components to execute in.
The basic deployment diagram element is the node. The node represents the environment in which a component or a set of components execute. This means that a node in a deployment diagram can represent a multitude of things—physical hardware such as a server machine, a system software like an operating system, or even application infrastructure software like a Web server, application server, database server, and so forth. The different nodes in the deployment diagram can be interconnected to represent interdependencies, thus providing a deployment diagram that is easy to comprehend and provides the complete deployment environment of a system.
Elements of a Deployment Diagram:
A deployment diagram consists of the following elements:
Design Patterns for a Secure Web application
-Satya Prakash
Introduction:
Building a secure application is not as simple as adding a password protected login screen. This article describes a collection of patterns to be used when dealing with the application security. In this article I am going to discuss about Single Access Point, Check point, Roles, Session, Limited View and Full View with Errors as these are widely used across the IT industry.
Single Access Point:
An army base provides a prime example of a secure location. Army personnel are allowed in while spies and reporters must be kept out. If the base has many entrances, it will be much difficult and expensive to guard each of them. Security is easier to guarantee when everyone must pass through a single guard station.
A security model is difficult to validate when it has multiple “front doors”, “back doors” and “side doors” for entering the application. The application will need a way to log a user into the system, to set up what the user can and can’t do and to integrate with other security modules from systems that will be interacting with. Single Access Point is a right solution for this problem by providing a secure place to validate users and collect global information needed about users who need to start using the application. This information is passed through some sort of Check Point that verifies the information. A Session is then created based upon the configuration settings and user’s access privileges. This Session is used to keep track of the global information that deals with the user’s current interaction with the application. When opening up any sub-application, requests are forwarded through the Check Point for handling any problems and validations.
Check Point:
Army Personnel working at a base have a security badge which is checked by the guard at front gate. They also have keys which will allow them to enter only areas in which they are authorized. No one is allowed in without a badge. Anyone who tried to enter a restricted area without clearance is dealt with severely.
At the Single Access Point, Checks must be made to verify that a user is permissible. Unfortunately, these checks could make getting into wrong password. While users may often mistype their passwords, frequent, consecutive failures without success could indicate that someone is trying to guess a password and break into the application. Application security should be designed in such a way that it must allow occasional mistakes while doing its best to keep a hacker out. Being a developer we could design many checks to determine if a user is trying to break into the system or is just making common mistakes in an efficient way. Check Point helps out with this by organizing these checks. The solution is Make an object that encapsulates the algorithm for the organization’s security policy. This object keeps track of how many exceptions should happen and decides what actions need to be taken based on the severity of the security violation. Any security check can be made part of the Check Point Algorithm, from password checks to authorization checks. In most of the systems, this pattern is separated into two conceptual parts: authentication and authorization. The combination of Single Access Point and Check Point provides authentication to the system and the combination of Check Point and Roles (user’s Role) provides proper authorization to the system.
Roles:
Every army base has commander. This commander gives the order if the base is to be shut down or brought to full alert status. These commands are privileges of the office of the commander, not of the particular person who holds that position. When the base commander is transferred or retires, a new person holds the position of base commander. “Base Commander” is that person’s Role.
Ensuring security can be more complicated in multi-user applications. Users have different areas of the application that they can see, can change, and control. When the number of users is large, the security permissions for users often fall into several categories like user’s job titles, experience or department. Ultimately, the administrator will struggle with managing the security profiles for large number of users. The administrator needs an easier way to manage permissions. The best way to achieve this is Create one or more role objects that define the permissions and access rights on different actions that group of users should have.
When a user logs in, he is assigned a set of privileges that specify what data is accessible and which parts of the application can be activated. From an administrator’s standpoint this user-privilege relationship is M-to-N, making it difficult to manage.
Introducing Roles creates two new relationships that must be managed: user-role and role-privilege. These new relationships can help managing security easier. When the privileges of a job title changes, then that role-privilege relationship can be edited directly. When a user gets a promotion, the user-role relationship can be changed instead of checking each user-privilege relationship for accuracy.
Session:
Army personnel’s activities are tracked while they are in high-security Defense bases. Their entry and exit are logged. Their badges must be worn at all times to show they are only where they are supposed to be. Security personnel inside the base can assume personnel with a badge have been checked thoroughly at the base entrance. Therefore they only have to perform minimal checks before allowing them into a restricted area. Many people will be working in a base at the same time. Each security badge (similar to Session Id of an application) uniquely identifies who that person is and what they can do. It also tracks what the carrier of the badge has been doing.
Secure applications need to keep track of global information used throughout the application such as username, roles and their respective privileges. To achieve this Create a Session object which holds all the variables that needs to be shared across many objects. This session object is then passed across the application so that any objects which need any of its values can access easily. Certain user information is used throughout the system. Some of this information is security related, such as the user’s role and privileges. A Session object is a good way for sharing this global information. This object can be passed around application and used as needed.
Full View With Errors:
Once army personnel allowed on an army base he or she could go to any building on the base. In effect, the officer has a full view of the buildings on the base. If the personnel try to enter a restricted area without proper clearance, either someone would stop them and say that they are not allowed in the restricted area or alarm would sound and guards would stop them.
GUI applications often provide multiple ways to view data. Users can dynamically choose which view on which data they want. When the application has multiple views, the developer must always be concerned with which operations are legal based on the current state of the application and the privileges of the user.
The conditional code for determining whether an operation is legal can be very complicated and difficult to test.
The solution for this is Design the system in such a way that all users can see everything of the system. When a user tries to perform any operation, check if it is valid. Notify the user with an error message when they perform illegal operations. This pattern fits best in applications where a user can perform almost any operation as user will be notified with very less number of error messages. Oracle Database is the best example to explain this pattern. When you access Oracle Database through SQL Plus, you can execute any command. However if you try to access data on which you don’t have privileges, then an appropriate error message will be shown.
Limited View:
When any higher official of army visits a base, he is given an escorted tour. Before arrival, a tour would be set up. Some areas of the base, such as the missile’s target range would be designed as unsafe and other might be designated top secret. The tour will be predesigned to give him a limited view of the base relevant to his security clearance.
Graphical applications often provide many ways to view data. Users can dynamically choose which view on which data they want. When an application has multiple views, the developer must always be concerned with which operations are legal given the current state of the application and the privileges of the user. The conditional code for determining whether an operation is legal can be very complicated and difficult to test. By limiting the view to what the user has access to, conditional code can be avoided. The solution is only let the users see what they have access to. When the application starts up, the user will have some Role or the application will default to some view. Base upon this Role, the system will only allow the user to select items that the current Role allows. If the user can not edit the data, then do not present the user with these options through menus or buttons.
Maven
-Ramesh Bacha
What is Maven?
......................................................................................................................................
Ø Introduction
Maven, a Yiddish word meaning accumulator of knowledge, was originally started as an attempt to simplify the build processes in the Jakarta Turbine project. There were several projects each with their own Ant build files that were all slightly different and JARs were checked into CVS. We wanted a standard way to build the projects, a clear definition of what the project consisted of, an easy way to publish project information and a way to share JARs across several projects.
The result is a tool that can now be used for building and managing any Java-based project. We hope that we have created something that will make the day-to-day work of Java developers easier and generally help with the comprehension of any Java-based project.
Ø Maven's Objectives
Maven's primary goal is to allow a developer to comprehend the complete state of a development effort in the shortest period of time. In order to attain this goal there are several areas of concern that
Maven attempts to deal with:
• Making the build process easy
• Providing a uniform build system
• Providing quality project information
• Providing guidelines for best practices development
• Allowing transparent migration to new features
Ø Making the build process easy
While using Maven doesn't eliminate the need to know about the underlying mechanisms, Maven does provide a lot of shielding from the details.
Ø Providing a uniform build system
Maven allows a project to build using its project object model (POM) and a set of plugins that are shared by all projects using Maven, providing a uniform build system. Once you familiarize yourself with how one Maven project builds you automatically know how all Maven projects build saving you immense amounts of time when trying to navigate many projects.
Ø Providing quality project information
Maven provides plenty of useful project information that is in part taken from your POM and in part generated from your project's sources. For example, Maven can provide:
• Change log document created directly from source control
• Cross referenced sources
• Mailing lists
• Dependency list
• Unit test reports including coverage
As Maven improves the information set provided will improve, all of which will be transparent to users of Maven. Other products can also provide Maven plugins to allow their set of project information alongside some of the standard information given by Maven, all still based on the POM.
Ø Providing guidelines for best practices development
Maven aims to gather current principles for best practices development, and make it easy to guide a project in that direction. For example, specification, execution, and reporting of unit tests are part of the normal build cycle using Maven. Current unit testing best practices were used as guidelines:
• Keeping your test source code in a separate, but parallel source tree
• Using test case naming conventions to locate and execute tests
• Have test cases setup their environment and don't rely on customizing the build for test preparation.
Maven also aims to assist in project workflow such as release management and issue tracking.
Maven also suggests some guidelines on how to layout your project's directory structure so that once you learn the layout you can easily navigate any other project that uses Maven and the same defaults.
Ø Allowing transparent migration to new features
Maven provides an easy way for Maven clients to update their installations so that they can take advantage of any changes that been made to Maven itself. Installation of new or updated plugins from third parties or Maven itself has been made trivial for this reason.
Ø What is Maven Not?
You may have heard some of the following things about Maven:
• Maven is a site and documentation tool
• Maven extends Ant to let you download dependencies
• Maven is a set of reusable Ant scriptlets
While Maven does these things, as you can read above in the "What is Maven?" section, these are not the only features Maven has, and its objectives are quite different.
Maven does encourage best practices, but we realise that some projects may not fit with these ideals for historical reasons. While Maven is designed to be flexible, to an extent, in these situations and to the needs of different projects, it can not cater to every situation without making compromises to the integrity of its objectives.
If you decide to use Maven, and have an unusual build structure that you cannot reorganise, you may have to forgo some features or the use of Maven altogether.
Maven Basics
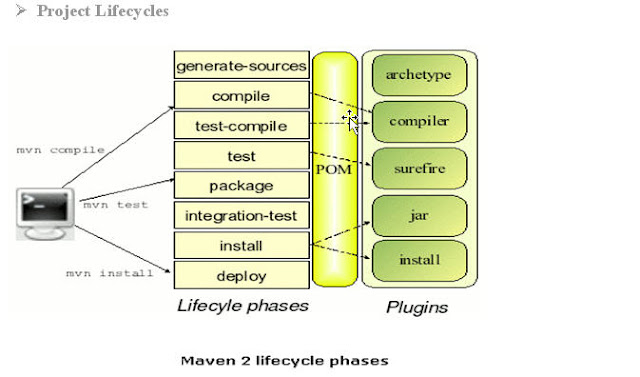
Ø The Project Object Model (POM)
• The heart of a Maven project is the POM
• Contains meta-data information of the project
• Versioning and configuration management
• Dependencies
• Project structure
• Application and testing resources
• Placed in project home directory as “pom.xml”
Ø POM.XML
<modelVersion>4.0.0</modelVersion>
<groupId>com.Ascential.com</groupId>
<artifactId>ASB-master</artifactId>
<packaging>war</packaging>
<version>1.0-SNAPSHOT</version>
<name>ASB master project</name>
<url>http://www.ascential.com/</url>
<dependencies>
<dependency>
<groupId>junit</groupId>
<artifactId>junit</artifactId>
<version>3.8.1</version>
<scope>test</scope>
</dependency>
</dependencies>
</project>
Feature Summary
----------------------------------------------------------------------------------------------------------------
The following are the key features of Maven in a nutshell:
• Simple project setup that follows best practices - get a new project or module started in seconds
• Consistent usage across all projects means no ramp up time for new developers coming onto a project
• Superior dependency management including automatic updating, dependency closures (also known as transitive dependencies)
• Able to easily work with multiple projects at the same time
• A large and growing repository of libraries and metadata to use out of the box, and arrangements in place with the largest Open Source projects for real-time availability of their latest releases
• Extensible, with the ability to easily write plugins in Java or scripting languages
• Instant access to new features with little or no extra configuration
• Ant tasks for dependency management and deployment outside of Maven
• Model based builds: Maven is able to build any number of projects into predefined output types such as a JAR, WAR, or distribution based on metadata about the project, without the need to do any scripting in most cases.
• Coherent site of project information: Using the same metadata as for the build process, Maven is able to generate a web site or PDF including any documentation you care to add, and adds to that standard reports about the state of development of the project. Examples of this information can be seen at the bottom of the left-hand navigation of this site under the "Project Information" and "Project Reports" submenus.
• Release management and distribution publication: Without much additional configuration, Maven will integrate with your source control system such as CVS and manage the release of a project based on a certain tag. It can also publish this to a distribution location for use by other projects. Maven is able to publish individual outputs such as a JAR, an archive including other dependencies and documentation, or as a source distribution.
• Dependency management: Maven encourages the use of a central repository of JARs and other dependencies. Maven comes with a mechanism that your project's clients can use to download any JARs required for building your project from a central JAR repository much like Perl's CPAN. This allows users of Maven to reuse JARs across projects and encourages communication between projects to ensure that backward compatibility issues are dealt with.
References


















